What can infect your computer and how scary it is. Take any hacker movie, and there will be something about viruses and Trojans. It may look beautiful and romantic on the screen, but what about real life?
Right off the bat: how to protect yourself
Viruses, Trojans and malicious programs exist. Next, we will describe them in detail, but first, how to protect yourself from all of them.
- Use anti-viruses. They will protect against most viruses, trojans and worms. You do not need to buy the most expensive and sophisticated antivirus, the basic versions are enough.
- If your operating system offers an update, install it. The update covers holes through which worms and viruses can get into your system.
- Use paid licensed programs, subscribe to official music services, and watch subscription shows, it’s cheap nowadays. Almost all malicious programs get on your computer through hacked software and sites like “Download soap operas without registration”.
- Back up important documents in the cloud and on external media – flash drives and hard drives.
- Treat the photo gallery on your phone as if it could be published on the web at any moment.
The best course of action in case of a serious infection of your computer or phone is to wipe your system clean. Look at them and think, “What if tomorrow I have to erase everything here?”
Viruses
A virus is a program that copies itself against your wishes. It can also do something harmful to you or useful to hackers, but what makes it a virus is its ability to spread. What they do is this.
- The virus ends up on your computer – you insert an infected flash drive, download a file from the Internet, or open a suspicious email.
- Using a spreading mechanism (each virus has its own mechanism), the virus launches itself and gets into RAM.
- The virus finds and infects files according to a certain principle – for example, all executable files or all files on flash drives. If the infected file is now run on another computer, the virus will be exposed and played there.
- At the same time, the virus does what it needs to do to the computer: it deletes data, formats disks, leaks your photos to the Net, encrypts files or steals passwords. This is optional and depends on the developer’s imagination.
Worms
These programs are similar to viruses, but with one difference: they have built-in mechanisms for spreading over the network, while a virus needs to be carried in files. To do this, worms exploit vulnerabilities in email programs, network protocols and operating systems. Simply put, you don’t need to do anything to get infected by a worm. The first network worm was the Morris worm. In November 1988, it infected 6,000 nodes on ARPANET, the future parent of the Internet. It was almost a disaster for the time because the worm disrupted network operations and caused $96 million in losses. More recently, in 2010, the Stuxnet worm was used to disrupt some industrial plants and collect data from important facilities such as airports, power plants and city systems. The same worm worked on Iranian nuclear facilities. Now, the threat of worms is decreasing because key network gateways are increasingly protected: when a worm crawls onto the “big Internet,” it can be immediately detected and stopped – but only if the worm is already known or is using an already discovered network vulnerability.

Trojans
Trojans don’t copy and launch themselves, but that doesn’t make them any less dangerous. They are named after the Trojan horse, in which Greek special forces entered Troy. Trojans on computers act in a similar way.
- Some useful program is taken. The hacker adds Trojan code to it. More often than not, it will be some hacked pirate software or a free music download program.
- When the user launches a useful program, two programs start working: the useful one, which was intended to run, and the harmful one, which quietly and unnoticed does something bad.
- The user may not even notice the first time something has gone wrong. A Trojan can run stealthily or “sleep” until a certain point.
- As a result, the Trojan can do anything: lock your computer, access it for other computers, or delete files.
People often download Trojans from the Internet under the guise of seemingly necessary programs: ad blockers, download gas pedals, the latest system optimizer, and so on. But in fact, these programs do little good and the risk of infecting your computer is high. So download software only from the official sites of manufacturers and developers. In the app stores for smartphones, you can find a lot of mysterious programs like “Flashlight”: they are free on the one hand, but when you start using them, they ask for access to contacts, files, photos, camera… Could it be that under the guise of a flashlight you get a spyware Trojan?
Spyware
A spyware program collects your data and sends it somewhere. The easiest option is waiting for you to start entering your credit card information somewhere in an online store, intercepting that data, and sending it to hackers. Spies can be part of a virus, worm, or Trojan. What else can spies do:
- keep track of all keystrokes and mouse movements;
- take screenshots;
- transfer your files to someone else’s server;
- record audio and video via microphone and webcam;
- watch what sites you visit to sell this data to advertisers.
If you think no one will be interested in spying on you, you’re wrong. Thousands of advertisers around the world hunt for accurate user data and some of them may use just such software. When the Pokemon Go fever began, many security experts were alarmed: the toy itself required access not only to the camera and geolocation but to almost the entire phone. What was this program doing in the background when people were catching Pokemon?
Ransomware and porn banners
Ransomware locks your computer and demands a ransom to unlock it, or encrypts files and demands a ransom to decrypt them. They spread like viruses, worms, or Trojans. Ransomware is created to make money, so the goal is to get the victim to pay as soon as possible. To create a sense of urgency, ransomware may say that there is so much time left before the files are destroyed. They may put shame on the victim: For example, they threaten the victim that child porn was found on their computer and is about to be turned over to the police. The confused victim would rather transfer the money than deal with it. A wave of such ransomware viruses swept the world a few years ago, and the most high-profile attack was the massive spread of Petya and NotPetya ransomware in 2016 and 2017. However, experts say that the ransomware was just a disguise, and in general, the hackers just wanted to do damage. Transferring money to the ransomware is, of course, not an option: first, most often they won’t unlock your computer afterwards; second, transferring money only inspires the ransomware to perform new labour exploits.
Advertising malware
Imagine: you are working as usual and once in 10 minutes an advertising window over the whole screen appears. After 20 seconds it disappears by itself. It’s not much of a nuisance, but it’s annoying. Or you go to the bank’s website, and you are directed to some affiliate site that offers to open a credit card without registration and SMS. What this means:
- Some unscrupulous webmaster is making money by spinning ads and attracting people to the sites.
- Since he is unscrupulous, he does not care about the quality of the audience. All he cares about is that the ads are shown.
- He creates an advertising virus that infects everything in a row and unrolls the desired ads on the computers of victims.
- For each display, the webmaster receives a penny.
- A kopeck to the world – for a dead man’s suit (somehow they say that).
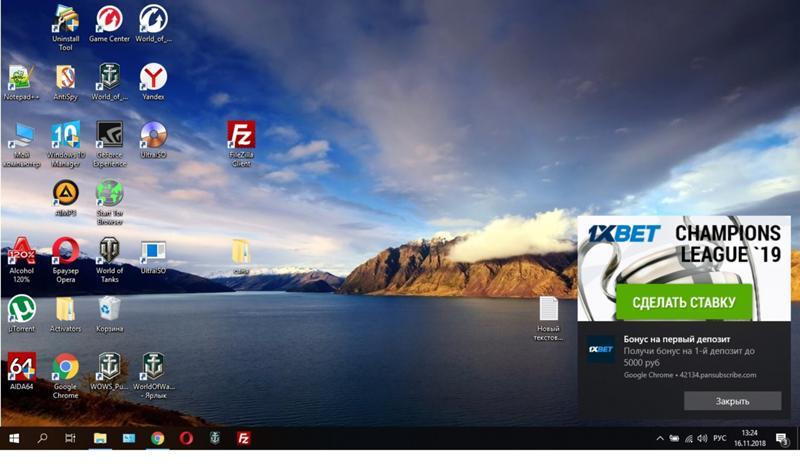
Adware themselves are not difficult to make and is most often spread by the Trojan model: you are offered some program like “Download music from VKontakte,” and along with it an adware Trojan is installed in the system. And when you uninstall the music program, the trojan remains. It is important to note that the advertising displayed by such Trojans will not necessarily be from unscrupulous advertisers. For example, in the screenshot below, 1XBet ads popped up – but this does not mean that this firm was involved in the creation of the malware. It’s more likely that they placed ads on some questionable (but legitimate) platform. The hackers registered on that site as an advertising site, but instead of the site, they injected advertising into the malware. And now they make money by unscrewing ads where they shouldn’t be.
Botnets
Botnets are groups of computers controlled from a single point and doing what the botnet master wants. If your computer becomes part of a botnet, it can be used quietly to attack other sites, send spam, or worse. For example, a hundred thousand people downloaded a “free TV shows” app. Together with the application (which might not work at all) an invisible service was installed on their computer. It does not manifest itself in any way and waits for a command from the “centre”. At some point, the “centre” receives an order to take down a site, such as a political opponent. “The “centre” commands its botnet: “Make a million requests to such and such a site. And the whole botnet, all 100,000 computers start doing it. The site overloads and stops working. This is called a DDoS attack – Distributed Denial of Service. It’s like all Muscovites being told to go to Auchan to buy buckwheat, and if they run out of buckwheat, don’t leave without a scandal. If your computer was part of a botnet, you may never even know about it, because all the requests happen in the background. But the damage from a massive botnet can be substantial. Botnets are not only made on desktop computers but also on smartphones. Imagine ten to twenty million smartphones in a huge botnet that will make several hundred requests per second for hours on end. A very dangerous weapon.
Miners
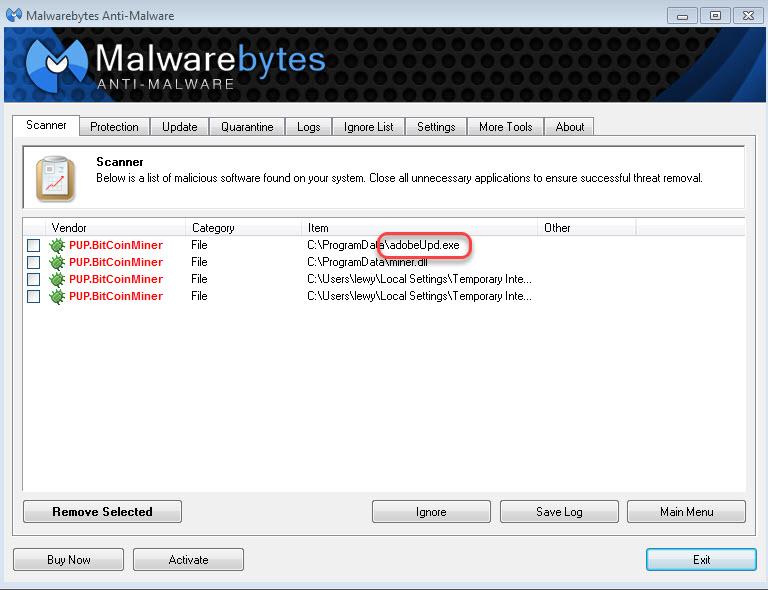
Botnets are needed from time to time, but cryptocurrency is always needed. You can combine business with pleasure by adding cryptocurrency mining capabilities to your program. One computer is unlikely to mine a whole bitcoin for an attacker, but a million computers in a botnet can. The harm of a miner is that it loads your processor to the brim, which reduces its service life, and the computer itself starts to slow down. And if you have a laptop that runs on battery power, a miner can drain it in half an hour. Miners embed inside hacked programs. The most recent example was when hackers hacked the music program Ableton Live and gave it away for free, but there was a miner on board. You can also sometimes find miners on websites. Of course, you will never find a miner in official software and on official sites. All this dirt and filth lives only in the realm of freebies, hacked programs and shows with no SMS. Be careful.
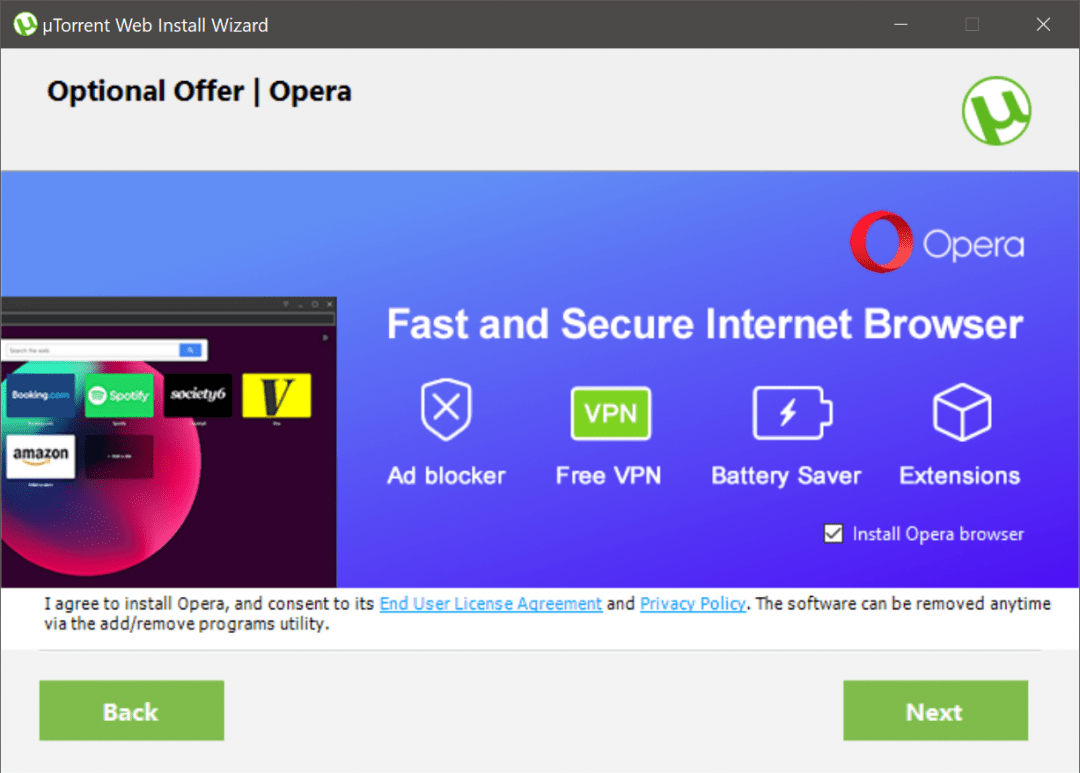
Bloatware
Let’s say you decide to download torrents. That’s not a crime in itself, so you go to the website of a popular torrent client and download the app. The official installer opens and you quickly scroll through all the screens. Then look – you have some new security system on your computer, instead of the standard browser is now “Opera”, and in the program panel, there are some new guys. Where did this come from?
If you look carefully, it turns out that when installing the torrent client, you unnoticeably did not uncheck the box with the associated installation of everything else. And now you have a whole zoo of unnecessary software in your memory – bloatware. If you have a high level of computer literacy, most likely you will be able to remove all the programs that suddenly struck. But if your parents or children are under attack, they might not be able to find their way. Bloatware itself is not always dangerous: it can be ordinary programs of different usefulness.
Bonus
In the end, you can see how antivirus works in different situations:
- when unpacking a program with a virus;
- launching a virus;
- what happens if I launch a virus and then turn on the anti-virus – will it disinfect or not?